Introduction
SMTP AUTH provides authentication of users over SMTP, allowing remote relaying for mobile users. More information on SMTP AUTH is available, along with general notes on sendmail on Mac OS X. In Mac OS X 10.2, Apple does not configure the built-in sendmail Mail Transport Agent (MTA) for SMTP AUTH support out of the box, nor do they ship the cyrus-sasl2 headers required to build sendmail with SASLv2 support.
These notes assume the Developer Tools have been installed on a Mac OS X 10.2 system, and that the reader is reasonably competent with Unix. The December 2002 developer tools update was installed on the test system used, which was running 10.2.5 at the time.
I know of no means by which sendmail can be linked to NetInfo; sendmail uses the SASL libraries to handle authentication. A SASL interface would need to be written that authenticates against NetInfo or via some Pluggable Authentication Module (PAM) interface. I have heard that the exim MTA may support NetInfo authentication as it does not rely on the SASL libraries to support SMTP AUTH.
Mac OS X 10.3 (Panther) ships with the postfix MTA. To use sendmail instead, install sendmail from source.
Cryus-SASL Setup
Mac OS X 10.2 ships with the cyrus-sasl2 libraries, which are used by Mail.app and other applications. However, in order to compile new software against these libraries, the header files also need to be installed, along with certain command line utilities.
- Obtain cyrus-sasl2.
- Verify cryus-sasl2.
- Expand cyrus-sasl2.
- Install header files.
- Install utilities (optional).
- Configure sendmail for sasl.
Download the latest cyrus-sasl2; this is version 2.1.13 at time of writing. Also download the *.sig signature file associated with the tarball in question.
Check that the signature for the tarball is valid with gpg.
$ gpg --verify cyrus-sasl-2*sig cyrus-sasl-2*gz
gpg: Signature made Mon Apr 14 12:41:37 2003 PDT using DSA key ID 5CE32FCC
gpg: Good signature from "Rob Siemborski <rjs3+@andrew.cmu.edu>"
gpg: aka "Rob Siemborski <robsiemb@crusoe.net>"
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Fingerprint: 0582 DCF3 F0EB 67D3 7F29 39BE 67AC F1C2 5CE3 2FCC
$ tar xzf cyrus-sasl-2*gz
$ sudo mkdir /usr/include/sasl
$ sudo cp cyrus-sasl-2*/include/*.h /usr/include/sasl
If the sasldb database will be used to authenticate users (as documented below), then the database utility saslpasswd2 will need to be manually compiled and installed using the following commands. I recommend installing the utility under /usr/local/sbin and adding that directory to your shell $PATH setting.
$ cd cyrus-sasl-2*
$ ./configure
$ (cd sasldb && make)
$ cd utils
$ cc saslpasswd.c -I.. -I../include -lsasl2 ../sasldb/.libs/libsasldb.al \
-o saslpasswd2
$ sudo cp saslpasswd2 /usr/local/sbin
The /usr/lib/sasl2/Sendmail.conf configuration file will need to be setup. The critical parameter is pwcheck_method, which sets the method by which sasl will lookup the username and password data received from sendmail. Using the sasldb database is one such method.
$ sudo -s
# echo "pwcheck_method: sasldb" > /usr/lib/sasl2/Sendmail.conf
If using sasldb, use the saslpasswd2 utility to create username and password entries for all the users in question in the database.
$ sudo saslpasswd2 -a Sendmail -c username
The saslpasswd2 must be compiled and installed under a directory listed under the $PATH environment variable to work, as with any Unix command. If the /usr/local/sbin directory is not in your $PATH, use the fully qualified path to where you installed the saslpasswd2 command to on your system:
$ sudo /usr/local/sbin/saslpasswd2 -a Sendmail -c username
Sendmail Compile
- Obtain sendmail sources.
- Configure sendmail for sasl.
- Build sendmail.
- Test for SMTP AUTH support.
- Install sendmail.
Obtain the latest version of sendmail (8.12.9 at time of writing), verify the sources with gpg, and expand the tarball.
Create a local site.config.m4 to enable SMTP AUTH support. The referenced file has support for SMTP AUTH and STARTTLS, among other things. The minimum required for SMTP AUTH support is listed as follows.
dnl SASL support
APPENDDEF(`confENVDEF', ``-DSASL=20113'')
APPENDDEF(`confLIBS', `-lsasl2.2.0.1')
dnl relay for authenticated users
define(`confAUTH_MECHANISMS', `GSSAPI DIGEST-MD5 CRAM-MD5 LOGIN PLAIN')
TRUST_AUTH_MECH(`GSSAPI DIGEST-MD5 CRAM-MD5 LOGIN PLAIN')
The 20113 number reflects the version of sasl header files installed in the previous step, while the 2.2.0.1 reflects the version of the sasl libraries installed by Apple under /usr/lib.
I usually place the site.config.m4 under /etc/mail for easy reference.
To build sendmail, use the Build script under the sendmail source directory with the -f option set to the fully qualified path to the custom site.config.m4 file. This will take some time, and print out many messages along the way.
$ cd sendmail-8.12*
$ sh Build -c -f /etc/mail/site.config.m4
First check that the new build of sendmail has SASLv2 support.
$ ./obj.*/sendmail/sendmail -d0 </dev/null | grep SASL
PIPELINING SASLv2 SCANF STARTTLS TCPWRAPPERS USERDB XDEBUG
Program mode requires special privileges, e.g., root or TrustedUser.
If so, confirm that the AUTH verb appears when running the new sendmail in test mode.
$ sudo ./obj.*/sendmail/sendmail -bs -Am
authfile_init=-1
220 legacy.local. ESMTP Sendmail 8.12.9/8.12.9; Sun, 20 Apr 2003 22:03:43 ↵
-0700 (PDT)
ehlo nurse
250-legacy.local. Hello root@localhost, pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE 5242880
250-DSN
250-ETRN
250-AUTH DIGEST-MD5 CRAM-MD5
250-STARTTLS
250-DELIVERBY
250 HELP
quit
221 2.0.0 legacy.local. closing connection
Note that the second test must be run as root. If the AUTH verb does not appear properly on your system, consult the logfile /var/log/mail.log for errors and try increasing the verbosity by running the second test as follows.
$ sudo ./obj.*/sendmail/sendmail -OLogLevel=25 -bs -Am
The new sendmail will use the default /etc/mail/sendmail.cf file, which may have not been configured properly. Setting up sendmail.cf for SMTP AUTH is covered later in these notes.
If the tests work properly, install the new sendmail to replace the default version installed on the system. In addition to installing sendmail with the Build script, also update the macro definition files under /usr/share/sendmail/conf. These files are used to build custom sendmail.cf and submit.cf files from *.mc files.
$ sudo sh Build install
$ sudo rsync --delete -rutvz cf/ /usr/share/sendmail/conf
Apple system updates may revert sendmail to the default version without SMTP AUTH support. Keep the sources for sendmail around so the customized version can be reinstalled easily, and check sendmail news sources to be informed when new versions of sendmail become available.
Sendmail Compile Problems
I have had reports that the -DSASL=20113 confENVDEF may cause Build to fail with sendmail.h parse errors such as the following, though have not been able to reproduce the problem.
../../sendmail/sendmail.h:143: parse error before "README"
../../sendmail/sendmail.h:203: warning: data definition has no type or ↵
storage class
../../sendmail/sendmail.h:1076: parse error before "ARGCLASS_T"
If this is the case, review the site.config.m4 and ensure the m4 macro values are properly quoted with a leading backticks and a trailing single quotes. Another option is to see if removing the =20113 option to -DSASL helps.
APPENDDEF(`confENVDEF', `-DSASL')
APPENDDEF(`conf_sendmail_LIBS', `-lsasl2.2.0.1')
APPENDDEF(`confINCDIRS', `-I/usr/include/sasl')
Sendmail Setup
The minimum required to have the sendmail daemon running on the system is as follows. Other configuration steps will need to be done to various /etc/mail configuration files, depending on the needs of the site in question.
Consider starting with my 8.12 domain server configuration and modifying it to suit the site in question. The configuration contains INSTALL notes that document how to customize the various files in question and supporting Makefile that eases the task of rebuilding the *.cf configuration files, updating hashed databases, and other administrative details.
- Edit /etc/mail/sendmail.mc, rebuild sendmail.cf.
- Run sendmail at startup.
- Start sendmail.
The minimum required parameters that will need to be added to a custom sendmail.mc to support SMTP AUTH are as follows. The confAUTH_MECHANISMS parameter specifies which SASL authentication methods should be enabled, and the TRUST_AUTH_MECH turns the server into an open relay for users who have authenticated using one of the specified mechanisms.
define(`confAUTH_MECHANISMS', `DIGEST-MD5 CRAM-MD5')
TRUST_AUTH_MECH(`DIGEST-MD5 CRAM-MD5')
I strongly advise against using the LOGIN and PLAIN authentication methods unless only permitted over STARTTLS tunnels. Plaintext authentication methods are prone to password sniffers, especially on shared segment subnets provided by certain broadband providers.
Once the custom /etc/mail/sendmail.mc is configured, sendmail.cf will need to be generated from it. If using my configuration installed properly under /etc/mail, this is simple to do.
$ cd /etc/mail
$ sudo make config
The make(1) command above requires a special /etc/mail/Makefile file to exist. Use the following Makefile; it has been modified to use the proper /usr/share/sendmail/conf CFDIR path for use on Mac OS X. Otherwise, sendmail.cf can be built manually via the following command.
$ sudo m4 /usr/share/sendmail/conf/m4/cf.m4 \
/etc/mail/sendmail.mc > /etc/mail/sendmail.cf
Set MAILSERVER to -YES- in /etc/hostconfig so sendmail starts when the system boots.
$ grep -i ^mail /etc/hostconfig
MAILSERVER=-YES-
See the /System/Library/StartupItems/Sendmail/Sendmail script for details on what is run. The queue run intervals specified with the -q option may need to be lowered for quicker delivery of temporarily delayed mail, depending on the site in question.
Sendmail can be started without a system reboot from the command line.
$ sudo /usr/sbin/sendmail -bd -q15m
$ sudo /usr/sbin/sendmail -C /etc/mail/submit.cf -q15m
The first command starts a sendmail daemon that listens for mail via the Simple Mail Transport Protocol (SMTP) at port 25 using the default sendmail.cf configuration file and the /var/spool/mqueue temporary queue directory. The second command launches a daemon that periodically checks for and attempts to resend any mail that ended up in /var/spool/clientmqueue.
Debugging
Be sure to watch /var/log/mail.log and /var/log/system.log for problems. Changing the LogLevel option temporarily in sendmail.cf to 25 should log more details to the logfiles, which may help debug a problem.
O LogLevel=25
To make sendmail.cf changes take effect, the main sendmail daemon will need to be restarted by sending it the HUP signal.
$ ps axo pid,command | grep sendmail
15213 /usr/sbin/sendmail -bd -q15m
15217 /usr/sbin/sendmail -C /etc/mail/submit.cf -q15m
$ kill -HUP 15213
To check whether sendmail is running properly, use ps(1) to see whether the daemons are running, and lsof(8) to check whether the main sendmail daemon is listening properly.
$ sudo lsof -i -P | grep ^sendmail
sendmail 15213 root 4u inet 0x02f311fc 0t0 TCP *:25 (LISTEN)
sendmail 15213 root 5u inet 0x02f3c4cc 0t0 TCP *:587 (LISTEN)
The telnet(1) command can be used to debug a local or remote SMTP server by connecting to port 25.
$ telnet 127.0.0.1 25
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
…
At a lower level, tools like tcpdump(1), tcpflow, and wireshark will allow debugging of the various protocols involved, from Domain Name Service (DNS) to SMTP.
Mail.app
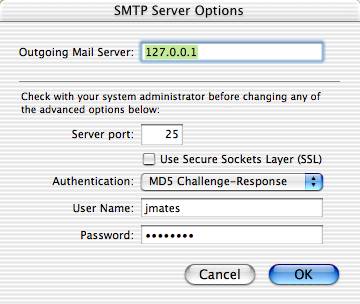
Testing of SMTP AUTH can be done with Mail.app on the server in question; set the Outgoing Mail Server to 127.0.0.1 and Authentication to MD5 Challenge-Response, if using the sasldb method in the Sendmail.conf configuration file.
Related
- Sendmail Configurations & Documentation
- SMTP AUTH and STARTTLS - presentation of the said mail protocols and their implementation in the Sendmail MTA.
- Relaying with TLS in Sendmail - how I configure my OS X laptop to do roaming Transport Layer Security (TLS) encrypted mail relaying through my main mail server.
